
Lab$Exercise$–$ ARP$$$
!
Objective)
To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to
join Ethernet and IP.
Requirements)
Wireshark: This lab uses the Wireshark software tool to capture and examine a packet trace. A packet
trace is a record of traffic at a location on the network, as if a snapshot was taken of all the bits that
passed across a particular wire. The packet trace records a timestamp for each packet, along with the
bits that make up the packet, from the lower-layer headers to the higher-layer contents. Wireshark runs
on most operating systems, including Windows, Mac and Linux. It provides a graphical UI that shows the
sequence of packets and the meaning of the bits when interpreted as protocol headers and data. It col-
or-codes packets by their type, and has various ways to filter and analyze packets to let you investigate
the behavior of network protocols. Wireshark is widely used to troubleshoot networks. You can down-
load it from www.wireshark.org if it is not already installed on your computer.
arp: This lab uses the “arp” command-line utility to inspect and clear the cache used by the ARP proto-
col on your computer. arp is installed as part of the operating system on Windows, Linux, and Mac
computers, but uses different arguments. It requires administrator privileges to clear the cache.
ifconfig / ipconfig: This lab uses the “ipconfig” (Windows) command-line utility to inspect the state
of your computer’s network interface. ipconfig is installed as part of the operating system on Win-
dows computers.
route / netstat: This lab uses the “route” or “netstat” command-line utility to inspect the routes
used by your computer. A key route is the default route (or route to prefix 0.0.0.0) that uses the default
gateway to reach remote parts of the Internet. Both “route” and “netstat” are installed as part of
the operating system across Windows and Mac/Linux, but there are many variations on the command-
line parameters that must be used.
Browser: This lab uses a web browser to find or fetch pages as a workload. Any web browser will do.

Address Resolution Protocol (ARP) Meaning
Address Resolution Protocol (ARP) is a protocol or procedure that connects an ever-changing Internet
Protocol (IP) address to a fixed physical machine address, also known as a media access control (MAC)
address, in a local-area network (LAN). This mapping procedure is important because the lengths of the
IP and MAC addresses differ, and a translation is needed so that the systems can recognize one another.
The most used IP today is IP version 4 (IPv4). An IP address is 32 bits long. However, MAC addresses are
48 bits long. ARP translates the 32-bit address to 48 and vice versa.
There is a networking model known as the Open Systems Interconnection (OSI) model. First developed
in the late 1970s, the OSI model uses layers to give IT teams a visualization of what is going on with a
particular networking system. This can be helpful in determining which layer affects which application,
device, or software installed on the network, and further, which IT or engineering professional is re-
sponsible for managing that layer.
The MAC address is also known as the data link layer, which establishes and terminates a connection be-
tween two physically connected devices so that data transfer can take place. The IP address is also re-
ferred to as the network layer or the layer responsible for forwarding packets of data through different
routers. ARP works between these layers.
)
What Does ARP Do and How Does It Work?
When a new computer joins a local area network (LAN), it will receive a unique IP address to use for
identification and communication. Packets of data arrive at a gateway, destined for a particular host
machine. The gateway, or the piece of hardware on a network that allows data to flow from one net-
work to another, asks the ARP program to find a MAC address that matches the IP address. The ARP
cache keeps a list of each IP address and its matching MAC address. The ARP cache is dynamic, but users
on a network can also configure a static ARP table containing IP addresses and MAC addresses.
ARP caches are kept on all operating systems in an IPv4 Ethernet network. Every time a device requests
a MAC address to send data to another device connected to the LAN, the device verifies its ARP cache to
see if the IP-to-MAC-address connection has already been completed. If it exists, then a new request is
unnecessary. However, if the translation has not yet been carried out, then the request for network ad-
dresses is sent, and ARP is performed.
An ARP cache size is limited by design, and addresses tend to stay in the cache for only a few minutes. It
is purged regularly to free up space. This design is also intended for privacy and security to prevent IP
addresses from being stolen or spoofed by cyberattackers. While MAC addresses are fixed, IP addresses
are constantly updated. In the purging process, unutilized addresses are deleted; so is any data related
to unsuccessful attempts to communicate with computers not connected to the network or that are not
even powered on.
What is address resolution protocol's relationship with DHCP and DNS? How do they differ?
ARP is the process of connecting a dynamic IP address to a physical machine's MAC address. As such, it is
important to have a look at a few technologies related to IP. As mentioned previously, IP addresses, by
design, are changed constantly for the simple reason that doing so gives users security and privacy.
However changes on IP addresses should not be completely random. There should be rules that allocate
an IP address from a defined range of numbers available in a specific network. This helps prevent issues,
such as two computers receiving the same IP address. The rules are known as DHCP or Dynamic Host
Configuration Protocol.
IP addresses as identities for computers are important because they are needed to perform an internet
search. When users search for a domain name or Uniform Resource Locator (URL), they use an alphabet-
ical name. Computers, on the other hand, use the numerical IP address to associate the domain name
with a server. To connect the two, a Domain Name System (DNS) server is used to translate an IP ad-
dress from a confusing string of numbers into a more readable, easily understandable domain name,
and vice versa.
What is ARP in Networking Useful For?
ARP is necessary because the software address (IP address) of the host or computer connected to the
network needs to be translated to a hardware address (MAC address). Without ARP, a host would not
be able to figure out the hardware address of another host. The LAN keeps a table or directory that
maps IP addresses to MAC addresses of the different devices, including both endpoints and routers on
that network.
This table or directory is not maintained by users or even by IT administrators. Instead, the ARP protocol
creates entries on the fly. If a user's device does not know the hardware address of the destination host,
the device will send a message to every host on the network asking for this address. When the proper
destination host learns of the request, it will reply back with its hardware address, which will then be
stored in the ARP directory or table. If ARP is not supported, manual entries can be made to this direc-
tory.

ARP Spoofing/ARP Poisoning Attack
ARP spoofing is also known as ARP poison routing or ARP cache poisoning. This is a type of malicious at-
tack in which a cybercriminal sends fake ARP messages to a target LAN with the intention of linking their
MAC address with the IP address of a legitimate device or server within the network. The link allows for
data from the victim's computer to be sent to the attacker's computer instead of the original destina-
tion. ARP spoofing attacks can prove dangerous, as sensitive information can be passed between com-
puters without the victims' knowledge. ARP spoofing also enables other forms of cyberattacks, including
the following:
Man-in-the-Middle (MTM) Attacks
A man-in-the-middle (MITM) attack is a type of eavesdropping in which the cyberattacker intercepts, re-
lays, and alters messages between two parties—who have no idea that a third party is involved—to
steal information. The attacker may try to control and manipulate the messages of one of the parties, or
of both, to obtain sensitive information. Because these types of attacks use sophisticated software to
mimic the style and tone of conversations—including those that are text- and voice-based—a MITM at-
tack is difficult to intercept and thwart. A MITM attack occurs when malware is distributed and takes
control of a victim's web browser. The browser itself is not important to the attacker, but the data that
the victim shares very much is because it can include usernames, passwords, account numbers, and oth-
er sensitive information shared in chats and online discussions. Once they have control, the attacker
creates a proxy between the victim and a legitimate site, usually with a fake lookalike site, to intercept
any data between the victim and the legitimate site. Attackers do this with online banking and e-
commerce sites to capture personal information and financial data.
Denial-of-Service Attacks
A denial-of-service (DoS) attack is one in which a cyberattacker attempts to overwhelm systems, servers,
and networks with traffic to prevent users from accessing them. A larger-scale DoS attack is known as a
distributed denial-of-service (DDoS) attack, where a much larger number of sources are used to flood a
system with traffic. These types of attacks exploit known vulnerabilities in network protocols. When a
large number of packets are transmitted to a vulnerable network, the service can easily become over-
whelmed and then unavailable.
Session Hijacking
Session hijacking occurs when a cyberattacker steals a user's session ID, takes over that user's web ses-
sion, and masquerades as that user. With the session ID in their possession, the attacker can perform
any task or activity that user is authorized to do on that network. Authentication occurs when a user
tries to gain access to a system or sign in to a restricted website or web service. The session ID is stored
in a cookie in the browser, and an attacker engaged in session hijacking will intercept the authentication
process and intrude in real time.
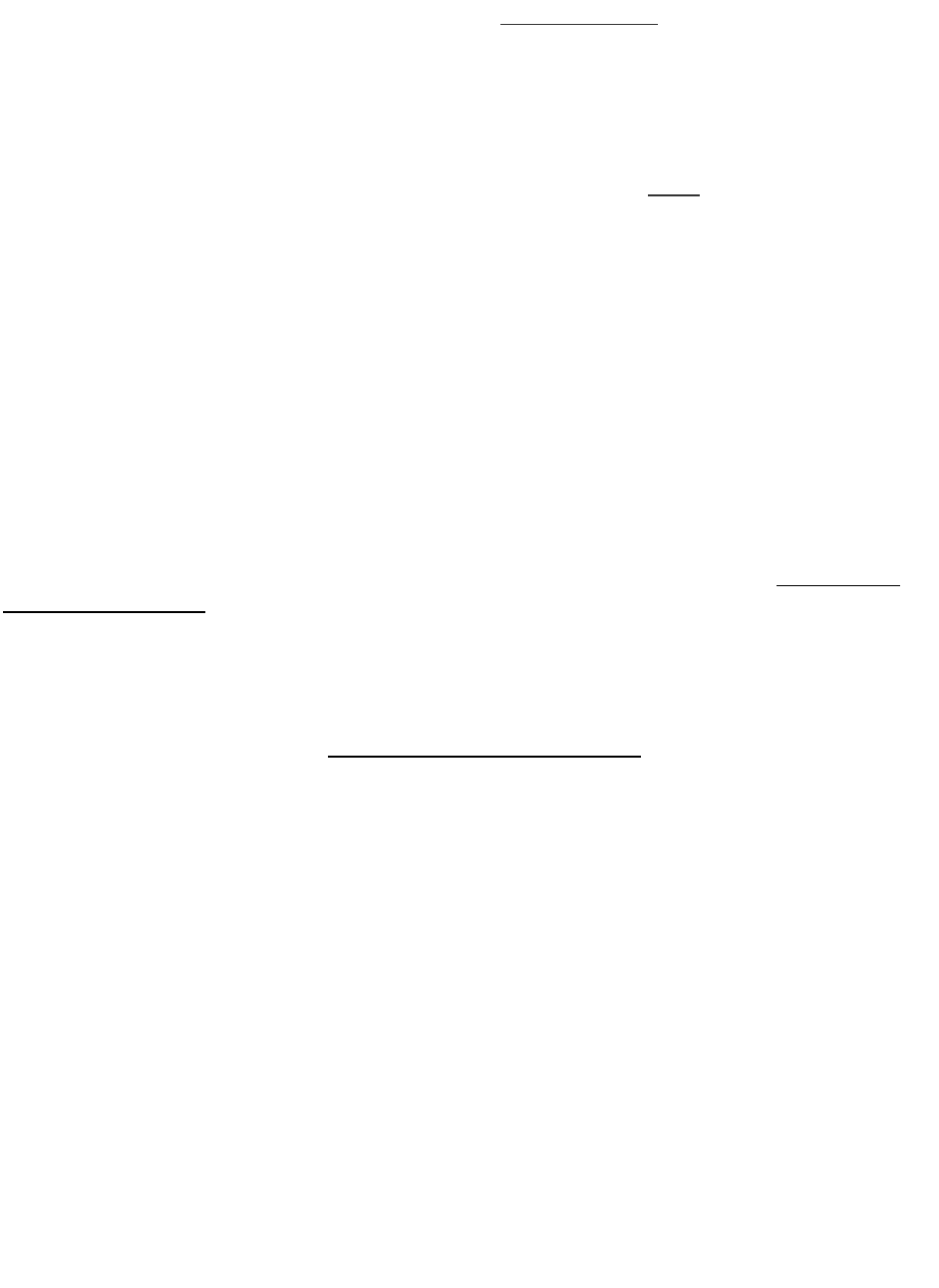
Lab)-)Network)Setup)
We want to observe the ARP protocol in action. ARP is used to find the Ethernet address that corre-
sponds to a local IP address to which your computer wants to send a packet. A typical example of a local
IP address is that of the local router or default gateway that connects your computer to the rest of the
Internet. Your computer caches these translations in an ARP cache so that the ARP protocol need only
be used occasionally to do the translation. The setup from the viewpoint of your computer is as shown
in the example below.
Figure 1: Network setup under which we will study ARP in second part
)
How ARP Works
When an incoming packet destined for a host machine on a particular local area network arrives at
a gateway, the gateway asks the ARP program to find a physical host or MAC address that matches the
IP address. The ARP program looks in the ARP cache and, if it finds the address, provides it so that the
packet can be converted to the right packet length and format and sent to the machine. If no entry is
found for the IP address, ARP broadcasts a request packet in a special format to all the machines on the
LAN to see if one machine knows that it has that IP address associated with it.
A machine that recognizes the IP address as its own returns a reply so indicating. ARP updates the ARP
cache for future reference and then sends the packet to the MAC address that replied.
There is a Reverse ARP (RARP) for host machines that don't know their IP address. RARP enables them to
request their IP address from the gateway's ARP cache.
Step)1:)Finding)your)IP)address)and)Gateway)address)
1. Open a command prompt. Please note that you cannot run as an administrator in the lab.
Simply type cmd:
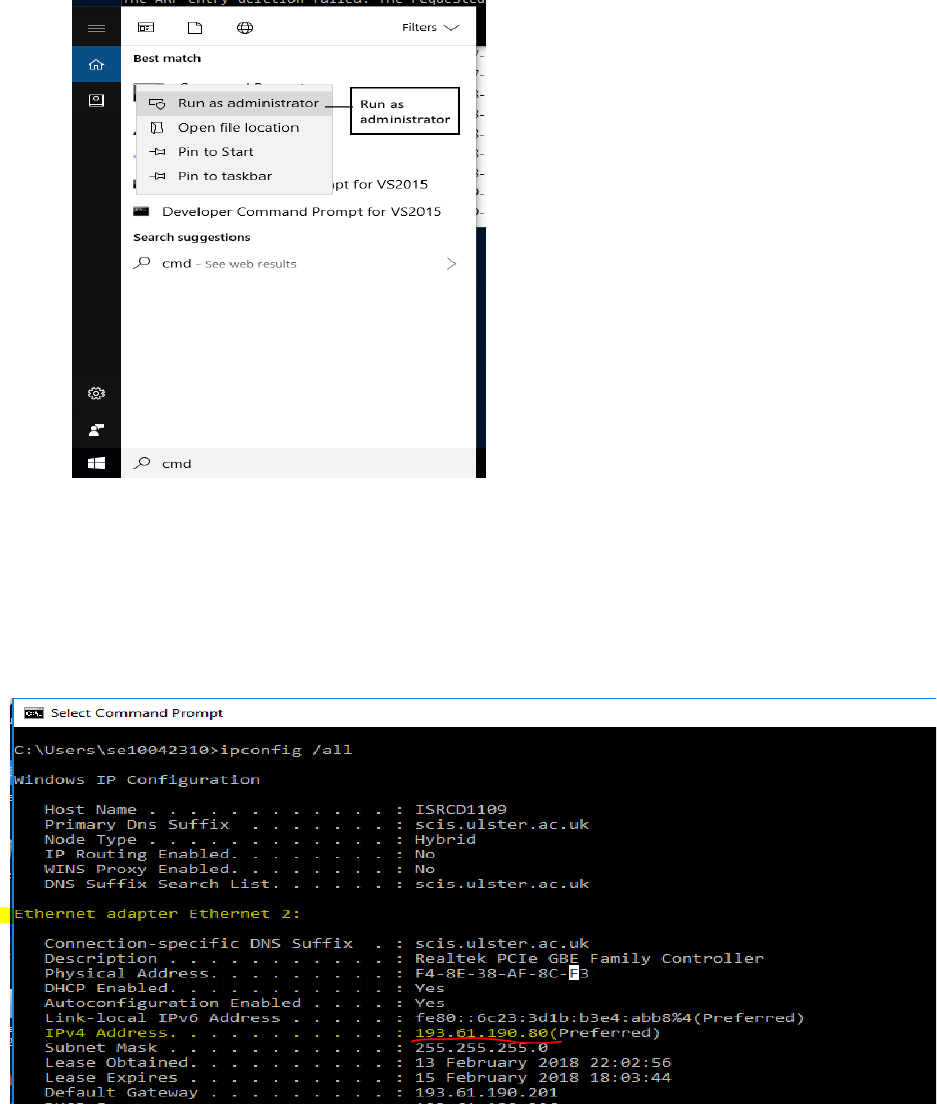
2. Find the Ethernet address of the main network interface OR the wireless address (see figure 3) of
your computer with the ipconfig command. You will want to know this address for later
analysis. On Windows, bring up a command-line shell and type “ipconfig /all”. Among the
output will be a section for the main interface of the computer (likely an Ethernet interface) and
its Ethernet address. Common names for the interface are “eth0” or “Ethernet adapter”. An ex-
ample is shown in figure 2, with added highlighting.
Figure 2: Finding the computer's Ethernet address with ipconfig (Windows)
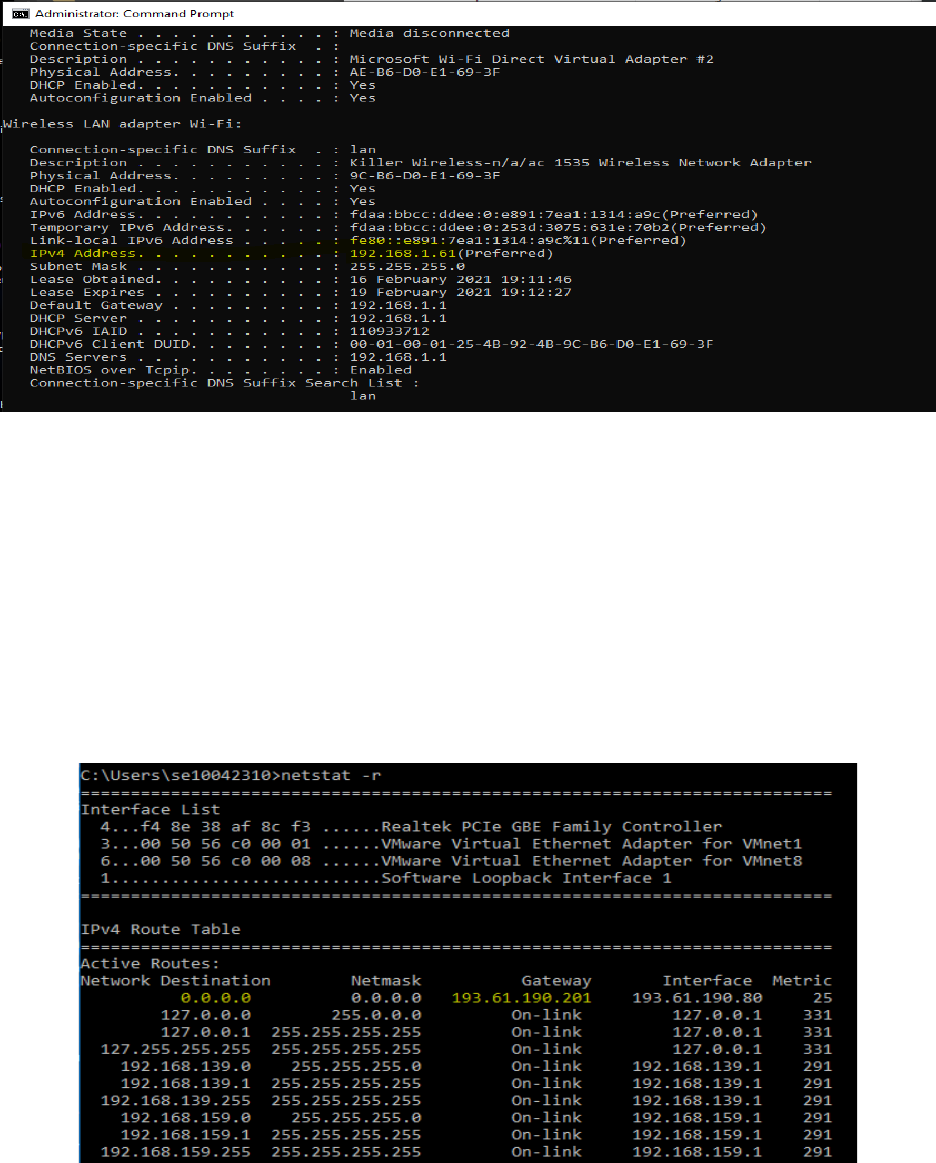
Figure 3: Finding the computer's WiFi IP address with ipconfig (Windows)
3. Find the IP address of the local router or default gateway that your computer uses to reach the
rest of the Internet using the netstat / route command. You should be able to use the
netstat -r command on Windows.
Alternatively, you can use the route command (“route print” on Windows). In either case
you are looking for the gateway IP address that corresponds to the destination of default or
0.0.0.0. An example is shown in figure 3 for netstat, with added highlighting.
Figure 4: Finding the default gateway IP address with netstat (Windows)
4. Now run Wireshark by typing “wireshark” in the bottom left search box in Windows
5. You should see the main Wireshark interface. Click on the Ethernet interface to start traffic
analysis on that interface.
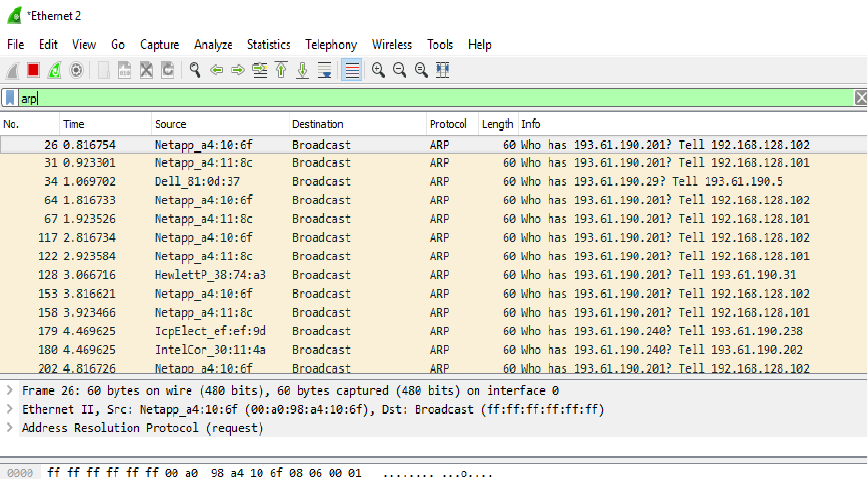
6. Add a filter of “arp”. Your capture window should be like the one pictured below.
Figure 6: Setting up the capture options
7. When the capture is started, use the “arp” command to clear the default gateway from the ARP
cache. Using the command “arp –a” will show you the contents of the ARP cache as a check
that you can run “arp”.
Go to command prompt and type arp -a as shown below.
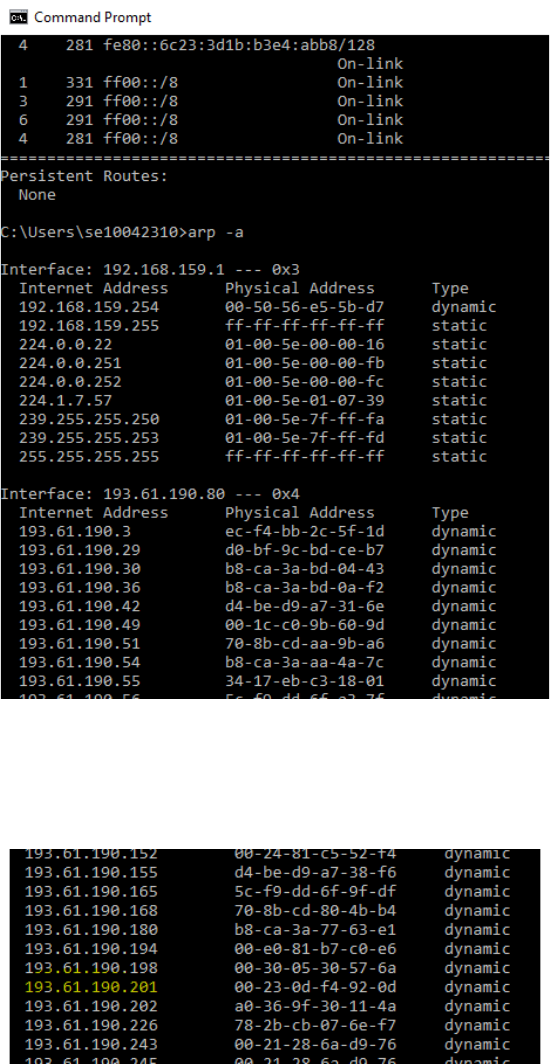
You should see an entry for the IP address of the default gateway as shown in image below. In
this case it is 193.61.190.201 which is the default gateway on my office PC.
8. To clear this entry, use the arp command with different arguments (“arp –d” on Windows) as
follows. Type arp -d in the command prompt.
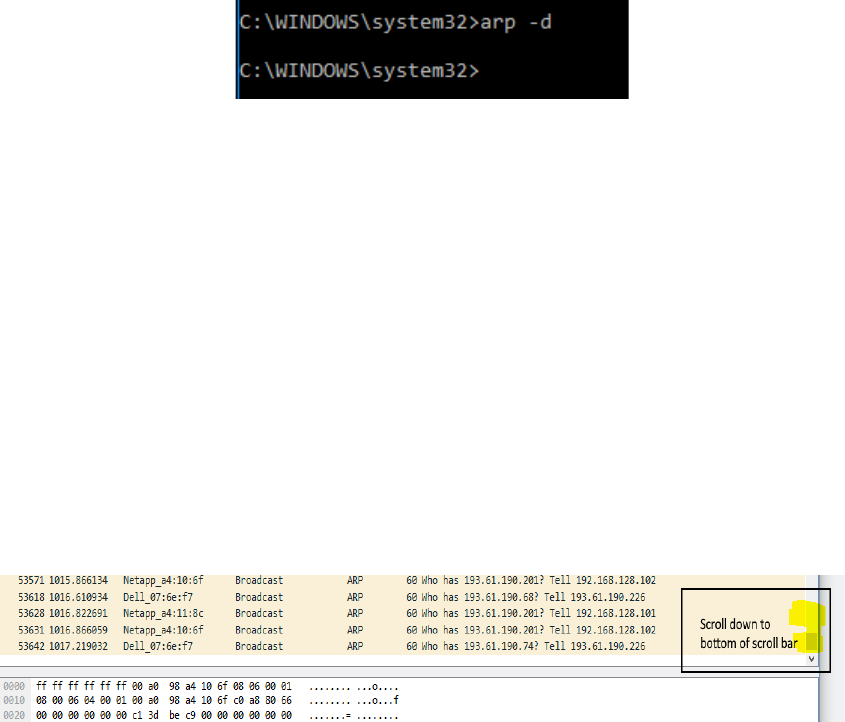
Note: This usage of arp will need administrator privileges to run, so you have to run as a privi-
leged user on Windows which is what you should have done in step 1. The command should run
without error, but the ARP entry may not appear to be cleared if you check with “arp –a”. This
is because your computer will send ARP packets to repopulate this entry as soon as you need to
send a packet to a remote IP address, and that can happen very quickly due to background activ-
ity on the computer.
9. Now that you have cleared your ARP cache, fetch a remote page with your Web browser. This
will cause ARP to find the Ethernet address of the default gateway so that the packets can be
sent.
10. You will see these packets flowing through your computer by scrolling down in the Wireshark
window to the bottom as shown below.
11. These ARP packets will be captured by Wireshark. You might clear the ARP cache and fetch a
document a couple of times. Hopefully there will also be other ARP packets sent by other com-
puters on the local network that will be captured. These packets are likely to be present if there
are other computers on your local network. In fact, if you have a busy computer and extensive
local network then you may capture many ARP packets. The ARP traffic of other computers will
be captured when the ARP packets are sent to the broadcast address, since in this case they are
destined for all computers including the one on which you are running Wireshark. Because ARP
activity happens slowly, you may need to wait up to 30 seconds to observe some of this back-
ground ARP traffic.
12. Once you have captured some ARP traffic, stop the capture. You will need the trace, plus the
Ethernet address of your computer and the IP address of the default gateway for the next steps.
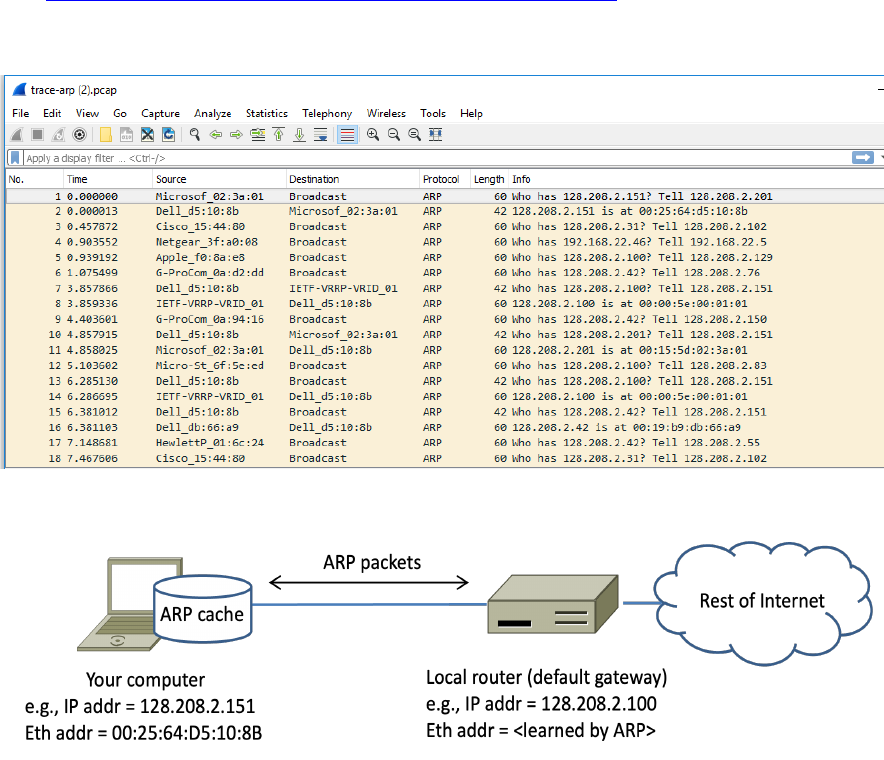
Step)2:)Inspect)the)supplied)AR P)Trace)
1. Close Wireshark.
2. Once Wireshark is closed, open the ARP trace here:
https://kevincurran.org/com320/labs/wireshark/trace-arp.pcap
You should see a screen as shown below.
The setup from the viewpoint of your computer from this trace is shown in the example below.
Figure 7: Network setup under which we will study ARP in this part
Note: Ethernet address of computer: 00:25:64:d5:10:8b and IP address of gateway: 128.208.2.100
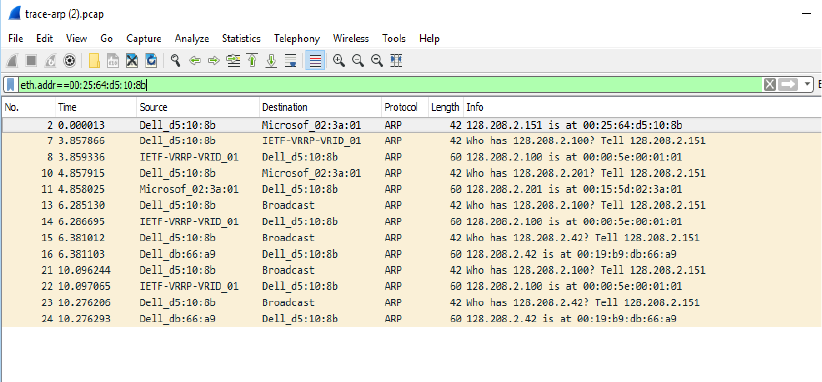
3. Now we can look at an ARP exchange. Since there may be many ARP packets in your trace, we’ll
first narrow our view to only the ARP packets that are sent directly from or to your computer.
Set a display filter for packets with the Ethernet address of your computer which is this case is
00:25:64:d5:10:8b.
You can do this by entering an expression in the blank “Filter:” box near the top of the
Wireshark window and clicking “Apply” or Enter. After applying this filter your capture should
look something like the figure below, in which we have expanded the ARP protocol details.
Figure 8: Capture of ARP packets, showing details of a request
Find and select an ARP request for the default gateway and examine its fields. There are two kinds of
ARP packets, a request and a reply, and we will look at each one in turn. The Info line for the request will
start with “Who has …”. You want to look for one of these packets that asks for the MAC address of the
default gateway, e.g., “Who has xx.xx.xx.xx …” where xx.xx.xx.xx is your default gateway. You can click
on the + expander or icon for the Address Resolution Protocol block to view the fields:
• Hardware and Protocol type are set to constants that tell us the hardware is Ethernet and the
protocol is IP. This matches the ARP translation from IP to Ethernet address.
• Hardware and Protocol size are set to 6 and 4, respectively. These are the sizes of Ethernet and
IP addresses in bytes.
• The opcode field tells us that this is a request.
• Next come the four key fields, the sender MAC (Ethernet) and IP and the target MAC (Ethernet)
and IP. These fields are filled in as much as possible. For a request, the sender knows their MAC
and IP address and fills them in. The sender also knows the target IP address – it is the IP ad-
dress for which an Ethernet address is wanted. But the sender does not know the target MAC
address, so it does not fill it in.
Next, select an ARP reply and examine its fields. The reply will answer a request and have an Info line of
the form “xx.xx.xx.xx is at yy:yy:yy:yy:yy:yy”:
• The Hardware and Protocol type and sizes are as set as before.
• The opcode field has a different value that tells us that this is a reply.
• Next come the four key fields, the sender MAC (Ethernet) and IP and the target MAC (Ethernet)
and IP just as before. These fields are reversed from the corresponding request, since the old
target is the new sender (and vice versa). The fields should now be all filled in since both com-
puters have supplied their addresses.
)
Step)3:)Details)of)ARP)over)Ethernet)
ARP packets are carried in Ethernet frames, and the values of the Ethernet header fields are chosen to
support ARP. For instance, you may wonder how an ARP request packet is delivered to the target com-
puter so that it can reply and tell the requestor its MAC address. The answer is that the ARP request is
(normally) broadcast at the Ethernet layer so that it is received by all computers on the local network in-
cluding the target. Look specifically at the destination Ethernet address of a request: it is set to
ff:ff:ff:ff:ff:ff, the broadcast address. So, the target receives the request and recognizes that it is the in-
tended recipient of the message; other computers that receive the request know that it is not meant for
them. Only the target responds with a reply. However, anyone who receives an ARP packet can learn a
mapping from it: the sender MAC and sender IP pair. The ARP header for a request and a reply is 28
bytes for both the request and reply for IPv4.
(Please note that answers on next page to following 5 questions)
To look at further details of ARP, examine an ARP request and ARP reply to answer these questions:
1. What opcode is used to indicate a request? What about a reply?
2. What value is carried on a request for the unknown target MAC address?
3. What Ethernet Type value which indicates that ARP is the higher layer protocol?
4. Is the ARP reply broadcast (like the ARP request) or not?
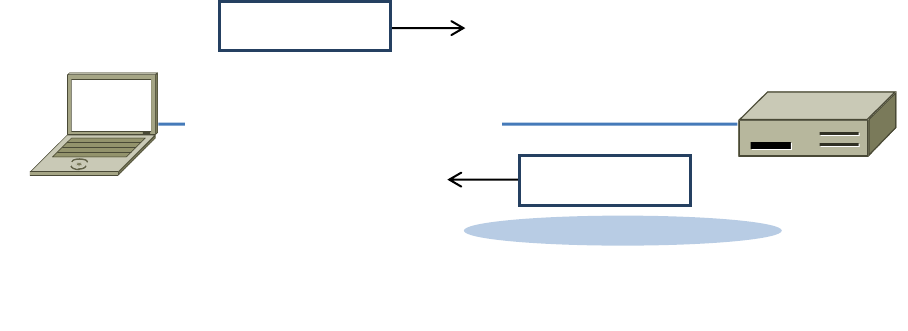
Answers)to)Step)3:)ARP)request)and)rep ly )
Figure 9: Details of the ARP request and reply to resolve the default gateway
There are several features to note:
• On the request, the target MAC is not known so it is usually filled in as 00:00:00:00:00:00.
• On the reply, the request target becomes the reply sender and vice versa.
• On the reply, the sender MAC returns the answer that is sought; it is highlighted.
• All of the fields that are shown are ARP header fields
Answers to the questions:
1. The request opcode is 1 and the reply opcode is 2.
2. The target MAC address of the request is normally all zeros, or 00:00:00:00:00:00.
3. The Ethernet Type value for ARP is 0x806.
4. The ARP reply is normally not broadcast. It is sent directly to the target using its Ethernet ad-
dress.
!
Your computer
Default gateway
Sender MAC=00:00:5E:00:00:01
Sender IP=128.208.2.100
Target MAC=00:25:64:D5:10:8B
Target IP=128.208.2.151
Request
Sender MAC=00:25:64:D5:10:8B
Sender IP=128.208.2.151
Target MAC=00:00:00:00:00:00
Target IP=128.208.2.100
Reply
